SAP Single Sign On works for both SAP and non-SAP applications, according to the vendor. It was developed by Secude, an SAP technology partner, and was acquired by SAP in 2011. It's based on standard security technologies, including Kerberos, X.509 digital certificates and SAML (Security Assertion Markup Language). I am doing same configuration but we are using SAP SSO Server 2 SP3. I think above videos & step are for version 1. Is the above video is applicable for SSO Server 2 SP3 also. If there are some changes so can you shame me the path or link for SSO server 2 SP3 version. Thanks in Advance. Fortunately, Single Sign-On users have the option of using digital certificates instead of the Single Sign-On user name and password to authenticate. This form of authentication involves an exchange of X.509 certificates between client and server over Secure Sockets Layer (SSL). SAP Single Sign-On offers support for X.509 certificates. X.509 certificates are highly interoperable, supporting both SAP and 3rd party web applications and clients, including many legacy systems. A reminder is sent to you if your single sign-on certificate is about to expire. Share tasks with your colleagues and work on projects collaboratively by adding search results or custom tasks to worklists. Avoid complications and unplanned efforts when implementing an SAP Note thanks to the SAP Notes Dependency Browser.
Skip Headers| Oracle9iAS Single Sign-On Administrator's Guide Release 2 (9.0.2) Part Number A96115-01 |
|
Single Sign-On using simple authentication poses a serious security risk. If hackers can access a Single Sign-On account, they can access numerous applications and do untold damage. Fortunately, Single Sign-On users have the option of using digital certificates instead of the Single Sign-On user name and password to authenticate. This form of authentication involves an exchange of X.509 certificates between client and server over Secure Sockets Layer (SSL).
Sap Single Sign On Configuration
This chapter covers the following topics:
- Benefits of Certificate-Enabled Single Sign-On
- Authentication Options
- Authentication Flow in Certificate-Enabled Single Sign-On
- System Requirements
- Configuring Single Sign-On for Certificates
- Troubleshooting Certificate-Enabled Single Sign-On
- Maintaining a Certificate Revocation List
Benefits of Certificate-Enabled Single Sign-On
Certificate authentication offers the benefit that partner applications are, by default, PKI enabled when the Single Sign-On Server is PKI enabled. As in Single Sign-On without certificates, these applications rely on cookies for authentication. Retrieving and checking a cookie requires less computing overhead than performing an SSL handshake. For Web applications characterized by short-lived sessions, the result is a significant improvement in server performance and throughput.

Authentication Options
Oracle Single Sign-On can be configured for SSL both with and without client certificates. The first option, server-side authentication, offers a strong degree of security. Still, the user's password is vulnerable to attack--either by guesswork or by brute force. Certificate-based authentication on both client and server sides, on the other hand, makes it difficult to sniff or modify data or to impersonate the client or server.
Authentication Flow in Certificate-Enabled Single Sign-On
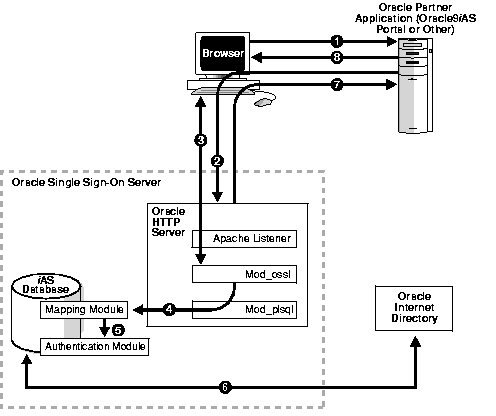
Figure 4-1 depicts the authentication flow for certificate-enabled Single Sign-On.
Figure 4-1 Certificate-Enabled Single Sign-On
Text description of the illustration ssoag005.gif
- The Single Sign-On user tries to access a partner application.
- The partner application redirects the user to the Single Sign-On server for authentication. The server must be configured so that, at the very least, it asks for optional client certification.
- If the server has been configured for SSL, the SSL handshake occurs. The browser prompts the user for a password that opens the browser certificate and key database. The browser then sends the user's certificate to the login URL of the Single Sign-On server.
- Mod_ossl, the SSL module on the Single Sign-On server, passes the user's certificate information to a PL/SQL module that maps the user's nickname and, optionally, his subscriber name.
- The mapping module passes the mapped user name and optional subscriber name to an authentication module.
- The authentication module uses the mapped user name to retrieve the user certificate stored in the directory; then it compares this certificate with the browser certificate received from mod_ossl.
- If the two certificates match, the Single Sign-On server signifies that authentication has been successful by passing a URLC token that contains user information to the application.
- The application redirects the user to the requested URL, which then delivers content.
System Requirements
The following criteria must be met before certificate-enabled Single Sign-On can proceed:
- The Single Sign-On server and Oracle Internet Directory, Oracle9iAS, Release 2, must be installed.
- The Oracle HTTP server must have a valid server certificate installed.
- The client certificate DN must be chosen in such a way that it contains some information about the Single Sign-On user name, or nickname, and, optionally, the subscriber name for this user name. The
cnattribute within the DN, for instance, might be the user's nickname (cn=jsmith). Anoattribute might be the user's subscriber name (o=acme). - The certificate of the client certificate issuer must be installed as a trusted certificate on the Single Sign-On server.
- The certificate of the server certificate issuer must be installed as a trusted certificate in the user's browser
Sap Single Sign On Options
Configuring Single Sign-On for Certificates
Certificate-enabled Single Sign-On is not a default option in Oracle9iAS, and it must be configured manually. The follow components may require configuration:
- Oracle HTTP Server (SSL)
- Mod_plsql
- User Name Mapping Module
- Oracle Internet Directory
- Single Sign-On Server
Oracle HTTP Server (SSL)
To configure the Oracle HTTP server, navigate to the server configuration file, using the following path:
Sap Single Sign On Certificate
In the SSL Virtual Host Context section of the httpd.conf file, add the parameters listed in Table 4-1:
Table 4-1 HTTP Parameters for Certificate-Enabled Single Sign-On

| Parameter | Description |
|---|---|
| The name of the server to be enabled for SSL |
| Setting the |
| The location, or path, of the server wallet |
| The verification type for client certificates. The options are as follows:
|
When configured properly, the SSL Virtual Host Context section of the httpd.conf file looks like this:
Mod_plsql
Configuring the plsql module for certificate-based authentication entails adding environment variables to the database access descriptor (DAD) for the Single Sign-On server. To add these variables, navigate to the DAD configuration file, using the following path:
In the dads.conf file, add the PlsqlCGIEnvironmentList parameter and the variables in Table 4-2.
Table 4-2 dads.conf Environment Variables
| Variable | Description |
|---|---|
SSL_CLIENT_S_DN_CN | The user's nickname, represented by the attribute |
SSL_CLIENT_S_DN_O | The subscriber name associated with the user, if any. The subscriber name is represented by the attribute |
SSL_CLIENT_S_DN | The distinguished name of the user |
SSL_CLIENT_CERT | The client certificate in base 64 format |
Mod_plsql must pass these variables to the user name mapping module.
When configured properly, the relevant section of the dads.conf file looks something like this:
User Name Mapping Module
The user name mapping module, which consists of the files ssodnmap.pks and ssodnmap.pkb, is located in the following directory:
If the user accepts the default implementation for the package, no file configuration is required. The default implementation assumes that the user's DN in the directory is the same as the certificate DN. The files ssodnmap.pkb and ssodnmap.pks are reproduced here for those who want to customize the module.
Oracle Internet Directory
For certificate-based authentication to be successful, the user certificate must be present in Oracle Internet Directory. If the certificate is issued by an in-house certificate authority or by the Oracle CA, it might be possible to publish the certificate in the directory automatically. If the certificate issuer is a third-party CA, a self-service application can fulfill this function.
Sap Single Sign-on With X.509 Certificates
To determine whether a self-service application is feasible, the directory administrator can try to add the certificate to the directory as an LDIF file, using the command-line tool ldapmodify.
The syntax for this command is as follows:
In the example LDIF file that follows, the certificate of user jsmith is represented as an attribute of his entry in the directory. The attribute type is usercertificate. The attribute value is the long string that follows.
Because it is a non-ASCII value, the certificate must be encoded in base 64 format, as shown here. Unlike other attributes, a base 64 attribute requires a double colon (::) as a delimiter. Note, too, that the use of a tab enables a base 64 attribute to be folded.
Single Sign-On Server
To enable the SSO server for SSL, all references to HTTP in SSO URLs must be changed to HTTPS. The script ssocfg.sh is provided for this purpose.
To run ssocfg.sh:
- Go to the directory that contains the script. The path is as follows:
- Enter the command, using the following syntax:
In this case, protocol is https. (To change back to HTTP, use http.) The parameter new_host is the host name of the HTTP listener for the Single Sign-On server. You can either assign a new host name or use an existing one. The parameter new_port is the port number of the listener, and sso_schema_name is the name of the SSO schema. The default schema name is orasso. This last parameter is optional.
Here is an example:
Port 443 is the default port number for single sign-on over SSL.
Troubleshooting Certificate-Enabled Single Sign-On
Use Table 4-3 to identify and solve problems that you are likely to face when configuring Oracle Single Sign-On for certificates.
Table 4-3 Troubleshooting Checklist for Certificate-Enabled Single Sign-On
Sap Single Sign On Install
| Problem | Cause | Solution |
|---|---|---|
The user tries to access a partner application over SSL and is presented with the error message 'Network Error: Connection Refused' Art of living soham audio review. | The | Add the missing parameter as specified in 'Oracle HTTP Server (SSL)'. If the parameter is present and is entered correctly, see if the Apache error log file identifies the problem. This file can be found at
|
The Single Sign-On login page fails to prompt the user for a certificate | The SSLVerifyClient optional parameter is missing from the httpd.conf file or has not been entered correctly | Add the missing parameter as specified in 'Oracle HTTP Server (SSL)'. If the parameter is present and is entered correctly, see if the Apache error log file identifies the problem. This file can be found at
|
Certificate authentication fails to work, and the user is presented the login page. | This problem has three possible causes:
|
|
Sap Single Sign On Portal
Maintaining a Certificate Revocation List
To ensure that users are unable to log in using invalid or expired certificates, the administrator must maintain an up-to-date certificate revocation list (CRL) on the Oracle HTTP server, and the CA that issued the certificate must provide this list. The file ca-bundle.crl can be used to maintain the list. At any rate, the path for the CRL file used must be as follows:
For details about implementing and maintaining a CRL, see comments in the httpd.conf file. The file is reproduced in the section 'Oracle HTTP Server (SSL)'.

Sap Single Sign On Certificate Form
Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|
